The OpenSSL Heartbleed Bug: What It Means To You
Below are steps for a Heartbleed resolution
The recent discovery of what's known as the 'Heartbleed' Bug in OpenSSL has caused great concern in the industry and you’ve no doubt heard about it by now. But what does it mean for you? Below are the simple steps you can take to resolve this issue. We advise you to complete these steps as soon as possible. Also, if you would like more information about the Heartbleed Bug, you can find that below as well.
Heartbleed Resolution Steps for DigiCert, GeoTrust, RapidSSL, and Thawte
- Step 1: To determine if you are vulnerable due to the Heartbleed bug, enter your domain name on https://www.ssllabs.com/ssltest/index.html. If your site is in the clear, then no action is needed J. However, if it is determined that your site is vulnerable, immediate action is advised and you should proceed to step 2.
- Step 2: Install the updated version of OpenSSL on your server. You can find this version right here: https://rhn.redhat.com/errata/RHSA-2014-0376.html. You can also read OpenSSL’s security advisory here: https://www.openssl.org/news/secadv_20140407.txt.
- Step 3: Generate a new Certificate Signing Request (CSR) and Private Key within the updated version of OpenSSL. The new CSR will be used to reissue the certificate and the new Private Key will be used to install the new SSL certificate once reissued.
- Step 4: Login to www.theSSLstore.com and click on "Total Orders".
- Step 5: Locate the certificate in question and click on the Order ID number.
- Step 6: Scroll down and click on the "Re-issue Certificate" button.
- Step 7: Paste in the new CSR which you retrieved from the new version of OpenSSL, fill in the rest of the required certificate details, and click ‘Submit’
- Step 8: After submission, the CA will require you to verify domain ownership again.
- Step 9: Once ownership has been proven, the certificate is reissued and you can proceed with installing your certificate on the new version of OpenSSL.
- Step 10: Please email us at [email protected] with your order number, old certificate's serial number and old certificate, our Support team will request the vendor to revoke old certificate manually.
Heartbleed Resolution for Comodo
- Step 1: To determine if you are vulnerable due to the Heartbleed bug, enter your domain name on https://www.ssllabs.com/ssltest/index.html. If your site is in the clear, then no action is needed. However, if it is determined that your site is vulnerable, immediate action is advised and you should proceed to step 2.
- Step 2: Install the updated version of OpenSSL on your server. You can find this version right here: https://rhn.redhat.com/errata/RHSA-2014-0376.html. You can also read OpenSSL's security advisory here: https://www.openssl.org/news/secadv_20140407.txt.
- Step 3: Generate a new Certificate Signing Request (CSR) and Private Key within the updated version of OpenSSL. The new CSR will be used to reissue the certificate and the new Private Key will be used to install the new SSL certificate once reissued.
- Step 4: Obtain your certificate serial number and save it to a notepad doc on your desktop. You’ll need this later to manually revoke your vulnerable certificate. You can retrieve this information by clicking on the padlock icon next to your URL. Please see below screenshots:
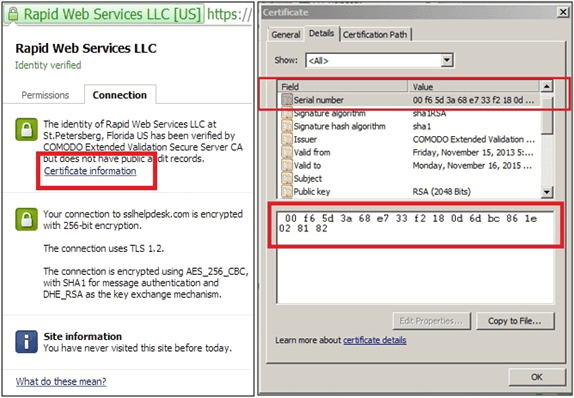
- Step 5: Login to www.theSSLstore.com and click on "Total Orders".
- Step 6: Locate the certificate in question and click on the Order ID number.
- Step 7: Scroll down and click on the "Re-issue Certificate" button.
- Step 8: Paste in the new CSR which you retrieved from the new version of OpenSSL, fill in the rest of the required certificate details, and click 'Submit'
- Step 9: After submission, the CA will require you to verify domain ownership again.
- Step 10: Once ownership has been proven and the certificate has been reissued, you can proceed with installing your certificate on the new version of OpenSSL.
- Step 11: After installation is complete, you then must manually revoke the old certificate. You can do this by clicking on the Revocation Button.

- Step 12: Once the Revocation Button has been clicked, you will be redirected to https://www.centralapi.com/heartbleed.aspx, where we will ask you for your username and password, along with your original order number and serial number to revoke the certificate.
What is Heartbleed?
On April 7th 2014, it was announced that OpenSSL versions 1.01 through 1.0.1f have a critical bug in their implementation of TLS Heartbeat Extension. This bug was nicknamed the Heartbleed Bug. Its official reference is CVE-2014-0160. It is important to note that OpenSSL versions 1.0.1g, 1.0.0, and 0.9.8 are NOT vulnerable.
OpenSSL is an open source package that an internet-user can use to get a quick access to TLS/SSL encryption. This bug was independently discovered by Condenomicon's team of security engineers – Riku, Antti and Matti, along with Neel Mehta from Google Security. It is believed to have been present in OpenSSL for more than two years. This vulnerability involved a bug which was found to be highly capable of paralyzing the older and reliable versions of general internet encryption procedures. The Heartbleed bug allows attackers to access a site’s content and the private (encryption) keys protecting the content.
This bug has sounded the alarm in the world of internet security, especially after considering the duration of exposure and the ease with which the bug exploited and attacked users’ private data being transmitted on the internet.
Affected Sites and Services
You can click here to access the list of all the possibly affected sites. But before signing off any site as ‘vulnerable', we recommend that you check their respective blogs for the latest updates. There is no way of telling how many sites out of the list were actually attacked as the bug leaves no trace of any attack carried out on the site.
Thankfully, names like Google, Amazon, and Microsoft have not yet found their way to the list.
How serious is the situation?
Theoretically, OpenSSL works just fine, but a tiny coding error like Heartbleed, and its aftermath, has made the software library and its popular versions vulnerable, so much so that the affected versions became capable of accessing private data from the site which was meant to be secured by TLS/SSL code.
In this situation, the attackers could theoretically take a look at the secret handshake a user is performing while logging into his email account. Username, password, and even credit card numbers may be at risk, depending on which service is being accessed by the e-mail user –although there is no way to know for sure. Attackers could also have a good look at how the site that is taking the data and identifies itself on the internet. Once half the handshake is compromised this way, the attackers can use their new-found private key to carry out man-in-the-middle attacks.
For more detailed information about the Heartbleed Bug, please visit: http://heartbleed.com/